 |
YAARX: Yet Another ARX Toolkit
0.1
|
 |
YAARX: Yet Another ARX Toolkit
0.1
|
YAARX is a set of programs for the differential analysis of ARX cryptographic algorithms. The latter represent a broad class of symmetric-key algorithms designed by combining a small set of simple operations such as modular addition, bit rotation, bit shift and XOR. More notable representatives of the ARX class of algorithms are the block ciphers FEAL, RC5, TEA and XTEA, the stream cipher Salsa20, the hash functions MD4, MD5, Skein and BLAKE as well as the recently proposed hash function for short messages SipHash.
YAARX complements existing toolkits such as ARXtools and significantly extends others, such as The S-function Toolkit. More specifically, YAARX provides methods for the computation of the differential probabilities of various ARX operations (XOR, modular addition, multiplication, bit shift, bit rotation) as well as of several larger components built from them. YAARX also provides means to search for high-probability differential trails in ARX algorithms in a fully automatic way. The latter has been a notoriously difficult task for ciphers that do not have S-boxes, such as ARX.
YAARX can help the cryptanalyst in the process of analyzing ARX-based constructions in at least two ways.
One way is to use the tools directly to compute differential probabilities for a target cipher. To this end YAARX provides a set of programs for the computation of the differential probabilities (DP) of several operations with user provided inputs. Such are for example the programs for computing the DP of modular addition, XOR, bit shift, etc.: adp_xor, xdp_add, adp_xor3, adp_xor_fixed_input, adp_rsh, adp_lsh, max_adp_xor, max_xdp_add, max_adp_xor3, max_adp_xor_fixed_input, eadp_tea_f, max_eadp_tea_f .
A conceivable scenario in this category would be the case in which the cryptanalyst constructs a differential characteristic by hand and wants to estimate its probability by computing the probabilities with which differences propagate through the ARX operations. In this case YAARX can provide answer to questions such as:
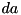 and
and 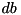 to an operation
to an operation 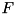 , and an output difference
, and an output difference 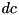 , what is the probability of the differential
, what is the probability of the differential 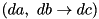 ?
? 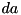 and
and 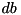 to
to 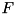 , what is the output difference
, what is the output difference 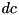 that has maximum probability?
that has maximum probability? 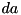 and an input value
and an input value 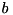 to
to 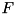 and an output difference
and an output difference 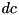 , what is the probability of the differential
, what is the probability of the differential 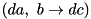 ?
? 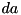 and a set of input differences
and a set of input differences 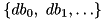 to
to 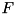 , and an output difference
, and an output difference 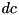 , what is the probability of the differential
, what is the probability of the differential 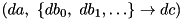 ?
? The differences 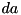 ,
, 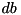 and
and 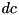 can be XOR or additive (ADD) differences and the operation
can be XOR or additive (ADD) differences and the operation 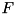 can either be one of the basic ARX operation, such as XOR, addition, etc. or a larger component e.g. a sequence of bit shift and XOR or of addition, rotation and XOR.
can either be one of the basic ARX operation, such as XOR, addition, etc. or a larger component e.g. a sequence of bit shift and XOR or of addition, rotation and XOR.
The second way in which YAARX can be useful would require a bit more effort and some programming literacy on the part of the cryptanalyst. The idea is, prior to using one of the YAARX tools, to first modify it according to ones' specific needs. This scenario is realistic in a case in which none of the YAARX tools is capable of directly addressing a problem for a given target cipher.
Scenarios in this category are likely to occur for example when one wants to automatically search for differential trails in a given cipher. While YAARX supports a general strategy for automatic search of trails, that is potentially applicable to many ARX algorithms, it is implemented for two specific ciphers, namely TEA and XTEA: tea_add_threshold_search, xtea_add_threshold_search, xtea_xor_threshold_search. Since the algorithmic technique underlying these implementations is general, the latter can be applied to other ARX algorithms after appropriate modifications. To facilitate this process, the source code is accompanied by extensive documentation.
For successful compilation it is required to install the development version of the GNU Scientific Library (GSL) and the Multiprecision arithmetic library (GMP) developers tools . Under Ubuntu/Debian Linux the name of the packages are resp. libgsl0-dev and libgmp-dev .
After downloading the YAARX source code, it can be compiled by running the make command from within the top directory of the source tree. The pre-compiled programs are stored in the ./bin directoy .
A list of the tools provided by YAARX, together with their computaional complexities is given in the table below. For more details on a specific algorithm refer to the documentation.
 Operator Operator | Algorithm | Description, (DP = differential probability, ADD = modular addition) | Complexity, ( |
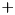 | 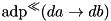 | The ADD DP of left shift (LSH). |
|
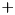 | 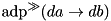 | The ADD DP of right shift (RSH). |
|
 | 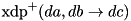 | The XOR DP (XDP) of ADD. |
|
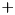 | 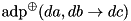 | The ADD DP (ADP) of XOR. |
|
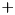 | 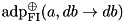 | The ADD DP of XOR with one fixed input. |
|
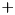 | 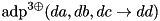 | The ADD DP of XOR with three inputs. |
|
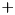 | 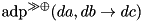 | The ADD DP of RSH followed by XOR. |
|
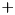 | 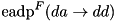 . . | The expected additive DP (EADP) of the F-function of TEA, averaged over all round keys and constants: 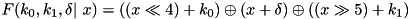 . . |
|
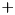 | 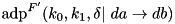 | The additive DP (ADP) of a modified version of the F-function of TEA with the shift operations removed: 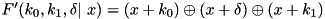 . . |
|
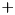 | 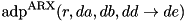 | The ADD DP of the sequence of operations ADD, ROT by 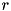 positions, XOR. positions, XOR. |
|
 | 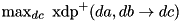 | The maximum XOR DP of ADD. |
|
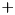 | 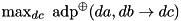 | The maximum ADD DP of XOR. |
|
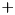 | 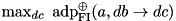 . . | The maximum ADD DP of XOR with one fixed input: |
|
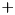 | 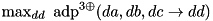 | The maximum ADD DP of XOR with three inputs: |
|
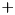 | 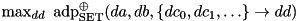 | The maximum ADD DP of XOR with three inputs, where one of the inputs satisfies a set of ADD differences. |
|
 | 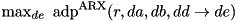 | The maximum ADD DP of ARX. |
|
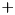 | 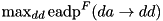 | The maximum expected additive DP (EADP) of the F-function of TEA, averaged over all round keys and constants: 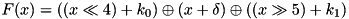 . . |
|
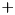 | 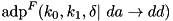 | The ADD DP of the F-function of TEA for a fixed key and round constants: 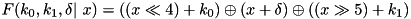 . . |
|
 | 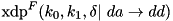 . . | The XOR DP of the F-function of TEA for a fixed key and round constants: 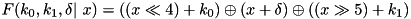 . . |
|
 | 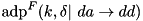 . . | The ADD DP of the F-function of XTEA for a fixed key and round constants: 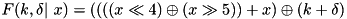 . . |
|
 | 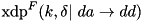 . . | The XOR DP of the F-function of XTEA for a fixed key and round constants: 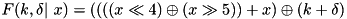 . . |
|
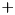 | 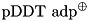 | Partial difference distribution table (pDDT) for 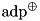 for a fixed probability threshold for a fixed probability threshold 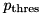 |
|
 | 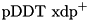 | Partial difference distribution table (pDDT) for 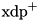 for a fixed probability threshold for a fixed probability threshold 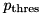 |
|
 | tea_add_threshold_search | Automatic search for ADD differential trails in block cipher TEA. | |
 | xtea_add_threshold_search | Automatic search for ADD differential trails in block cipher XTEA. | |
 | xtea_xor_threshold_search | Automatic search for XOR differential trails in block cipher XTEA. |
YAARX is developed in the Laboratory of Algorithmics, Cryptology and Security (LACS) of Luxembourg University and is licensed under GPL (c) 2012-2013.